Introduction
In today's digital landscape, web applications are a crucial part of businesses and organizations. However, with the increasing number of cyber threats, ensuring the security of these web applications is more important than ever. One way to enhance the security of web applications is by regularly scanning them for vulnerabilities using open-source tools.
In this article, we'll explore the importance of scanning web applications for vulnerabilities and how open-source tools can help in this regard.
Why Scan Web Applications for Vulnerabilities?
Web applications are often targeted by hackers looking to exploit vulnerabilities for various malicious purposes, such as stealing sensitive data, defacing websites, or launching attacks. By scanning web applications for vulnerabilities, organizations can identify and address security weaknesses before they are exploited by malicious actors.
- Prevention of Data Breaches: Security flaws in web applications may expose critical user data, such as personal details, financial information, and login credentials. Taking a proactive approach to identifying vulnerabilities can help prevent data breaches and ensure user privacy.
- Maintaining Trust and Reputation: A security breach can severely harm an organization's reputation and undermine the trust of its customers and stakeholders. Conducting regular vulnerability scans shows a strong commitment to security and helps preserve trust in the organization's digital services.
- Compliance Requirements: Countless industries need to meet regulatory requirements that emphasize the protection of important data. By proactively scanning for vulnerabilities, organizations can ensure they meet standards like GDPR, PCI DSS, HIPAA, and other relevant regulations.
- Cost Savings: Spotting and addressing vulnerabilities early in the development process is much more cost-efficient than dealing with the aftermath of a security breach. Leveraging scanning tools can help detect vulnerabilities in the early stages of development, reducing the expenses associated with fixing them later.
Open-Source Tools for Web Application Security Scanning
There are several open-source tools available for scanning web applications for vulnerabilities. These tools provide a cost-effective way to enhance the security of web applications without the need for expensive proprietary solutions. Some popular open-source tools for web application security scanning include:
- OWASP ZAP (Zed Attack Proxy): OWASP ZAP is a widely used open-source web application security scanner that helps identify vulnerabilities in web applications. It can be used both as a proxy to intercept and modify HTTP/HTTPS requests. It provides automated scanning capabilities, as well as features for manual testing and advanced penetration testing.
- Nikto: Nikto is another popular open-source web server scanner that performs comprehensive tests against web servers for multiple items, including dangerous files, outdated server software, and other potential security issues.
- Wfuzz: Wfuzz is a web application security testing tool that can help identify vulnerabilities such as SQL injection, XSS, and other common web application flaws by brute-forcing parameters.
- OpenVAS (Open Vulnerability Assessment System): OpenVAS is a comprehensive vulnerability scanner that detects security issues in networks and web applications. It includes a database of known vulnerabilities and provides regular updates to ensure accurate detection of emerging threats.
- Wapiti: Wapiti is a command-line-based web application vulnerability scanner that can identify various security issues, including SQL injection, cross-site scripting (XSS), and file inclusion vulnerabilities. It offers both black-box and white-box testing capabilities.
- NMAP: Nmap, short for Network Mapper, is a powerful open-source tool used for network discovery and security auditing. It scans networks to identify hosts, services, and open ports, providing valuable insights into network topology and potential vulnerabilities. You may refer my previous blog, how to use it. Click here.
Code Example Using OWASP ZAP
Here is a simple code example demonstrating how to use OWASP ZAP to scan a web application for vulnerabilities with python:
import time
from zapv2 import ZAPv2
target = 'http://example.com'
zap = ZAPv2()
print('Accessing target %s' % target)
zap.urlopen(target)
time.sleep(2)
print('Spidering target %s' % target)
zap.spider.scan(target)
time.sleep(10)
alerts = zap.core.alerts()
if alerts:
print('Alerts found:')
for alert in alerts:
print(alert)
else:
print('No alerts found.')
In this code example, we first specify the target web application URL, initialize the OWASP ZAP instance, access the target URL, and then perform a spider scan to identify vulnerabilities. Finally, we check for any alerts generated by the scan and print them if found.
Let's see another example, scanning site with Nikto, and saving the result in .htm formate.
nikto.pl --host https://www.bithost.in
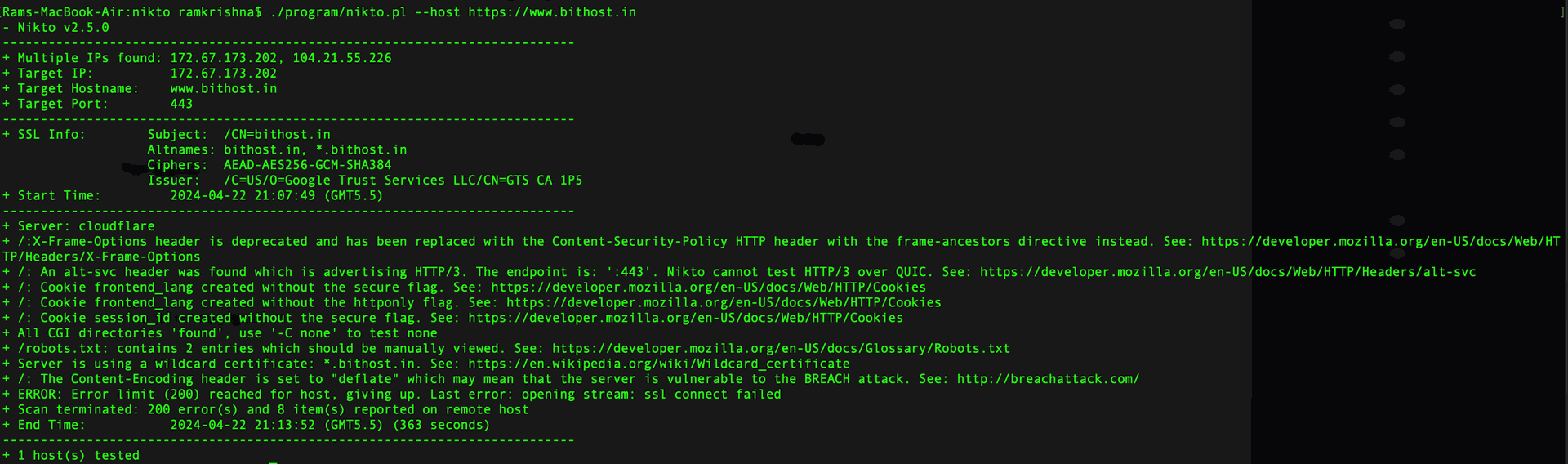
This scan is performed to demonstrate the key loopholes.
Let's see in other example how to save it .htm formate:
nikto.pl --host https://www.bithost.in -o custome-scan.htm

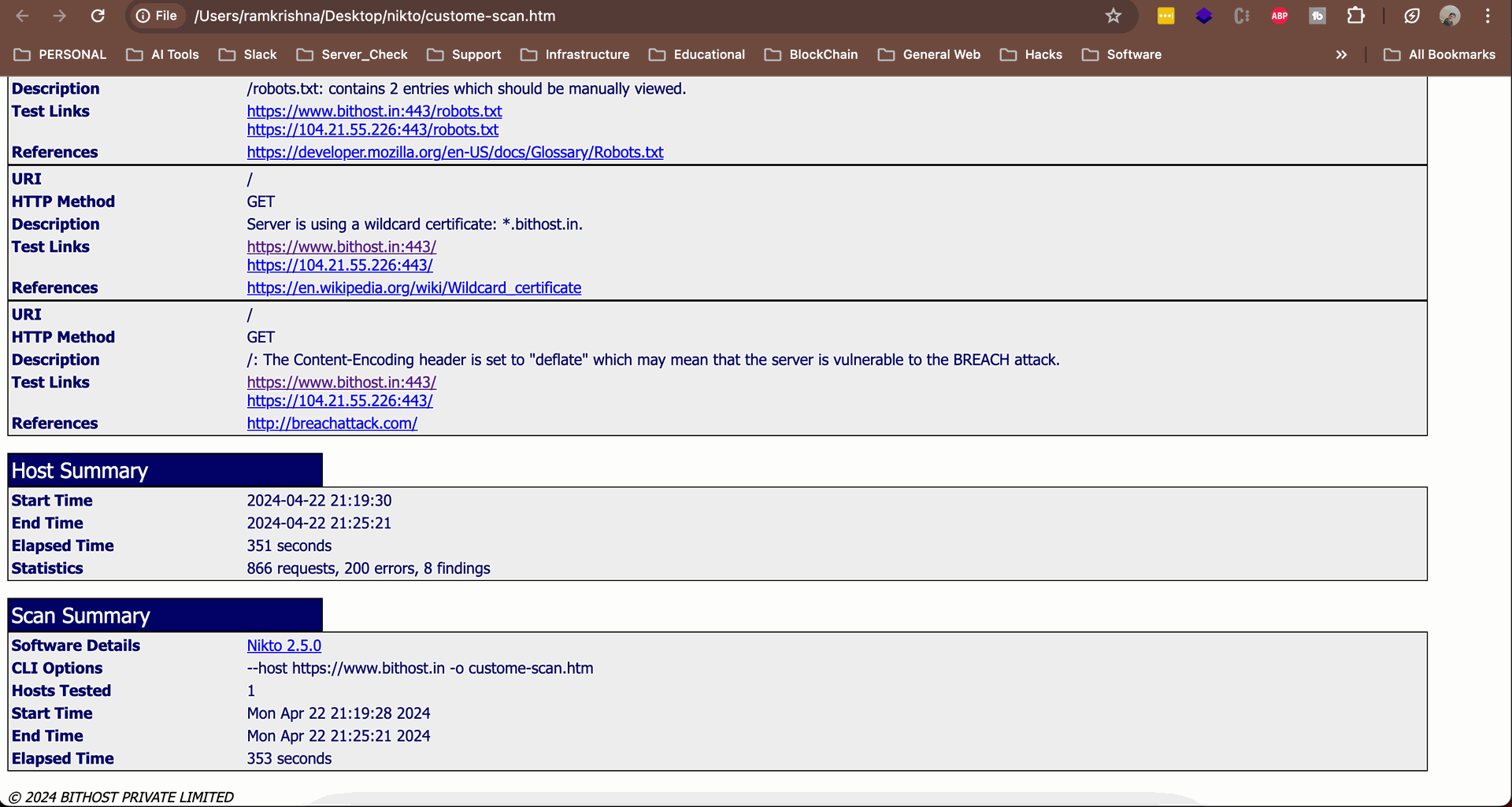
In this example you can see how the saved data is being shown after scan completes.
The footer section is a bit modified in scan template to show Bithost Private Limited copyright.
There are number of tools, you should be familiar with few of them to start your career in cyber security.
Conclusion
Scanning web applications for vulnerabilities using open-source tools is a proactive approach to enhancing security in today's digital landscape. By regularly scanning web applications for vulnerabilities, organizations can identify and mitigate security risks before they are exploited by malicious actors. Open-source tools like OWASP ZAP, Nikto, and Wfuzz provide effective ways to automate the security scanning process and ensure the integrity of web applications.
Remember, security is an ongoing process, and regular scanning and testing are essential to maintaining a secure web application environment.
For queries do comment and share with your friends...
Ensuring Security in Today's Digital Landscape with Open-Source Tools for Vulnerabilities Scan